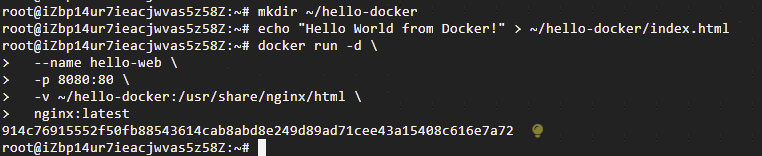
Binwalk
Binwalk 是一个非常强大的工具,可以用来分析和提取嵌入在二进制文件(如图片、固件等)中的压缩包、文件系统或其他数据。它能够自动识别图片文件中的嵌入数据,并提取出压缩包文件。
你可以用 Binwalk 对图片文件进行分析,命令行如下:
binwalk image.png
它会扫描文件内容,寻找嵌入的压缩包或其他数据格式。如果图片文件中嵌入了一个压缩包,Binwalk 会标识出压缩包的起始位置,显示文件类型及大小。
如果找到压缩包,使用 binwalk -e 可以直接提取它:
binwalk -e image.png
github项目:https://github.com/devttys0/binwalk
binwalk的wiki:https://github.com/devttys0/binwalk/wiki
推荐Linux安装,一条命令搞定!
apt install binwalk
root@iZbp14ur7ieacjwvas:~# binwalk
Binwalk v2.3.3
Craig Heffner, ReFirmLabs
https://github.com/ReFirmLabs/binwalk
Usage: binwalk [OPTIONS] [FILE1] [FILE2] [FILE3] …
Signature Scan Options:
-B, –signature Scan target file(s) for common file signatures
-R, –raw=<str> Scan target file(s) for the specified sequence of bytes
-A, –opcodes Scan target file(s) for common executable opcode signatures
-m, –magic=<file> Specify a custom magic file to use
-b, –dumb Disable smart signature keywords
-I, –invalid Show results marked as invalid
-x, –exclude=<str> Exclude results that match <str>
-y, –include=<str> Only show results that match <str>
Extraction Options:
-e, –extract Automatically extract known file types
-D, –dd=<type[:ext[:cmd]]> Extract <type> signatures (regular expression), give the files an extension of <ext>, and execute <cmd>
-M, –matryoshka Recursively scan extracted files
-d, –depth=<int> Limit matryoshka recursion depth (default: 8 levels deep)
-C, –directory=<str> Extract files/folders to a custom directory (default: current working directory)
-j, –size=<int> Limit the size of each extracted file
-n, –count=<int> Limit the number of extracted files
-0, –run-as=<str> Execute external extraction utilities with the specified user’s privileges
-1, –preserve-symlinks Do not sanitize extracted symlinks that point outside the extraction directory (dangerous)
-r, –rm Delete carved files after extraction
-z, –carve Carve data from files, but don’t execute extraction utilities
-V, –subdirs Extract into sub-directories named by the offset
Entropy Options:
-E, –entropy Calculate file entropy
-F, –fast Use faster, but less detailed, entropy analysis
-J, –save Save plot as a PNG
-Q, –nlegend Omit the legend from the entropy plot graph
-N, –nplot Do not generate an entropy plot graph
-H, –high=<float> Set the rising edge entropy trigger threshold (default: 0.95)
-L, –low=<float> Set the falling edge entropy trigger threshold (default: 0.85)
Binary Diffing Options:
-W, –hexdump Perform a hexdump / diff of a file or files
-G, –green Only show lines containing bytes that are the same among all files
-i, –red Only show lines containing bytes that are different among all files
-U, –blue Only show lines containing bytes that are different among some files
-u, –similar Only display lines that are the same between all files
-w, –terse Diff all files, but only display a hex dump of the first file
Raw Compression Options:
-X, –deflate Scan for raw deflate compression streams
-Z, –lzma Scan for raw LZMA compression streams
-P, –partial Perform a superficial, but faster, scan
-S, –stop Stop after the first result
General Options:
-l, –length=<int> Number of bytes to scan
-o, –offset=<int> Start scan at this file offset
-O, –base=<int> Add a base address to all printed offsets
-K, –block=<int> Set file block size
-g, –swap=<int> Reverse every n bytes before scanning
-f, –log=<file> Log results to file
-c, –csv Log results to file in CSV format
-t, –term Format output to fit the terminal window
-q, –quiet Suppress output to stdout
-v, –verbose Enable verbose output
-h, –help Show help output
-a, –finclude=<str> Only scan files whose names match this regex
-p, –fexclude=<str> Do not scan files whose names match this regex
-s, –status=<int> Enable the status server on the specified port
root@iZbp14ur7ieacjwvas:~#
binwalk常用命令
-e 分解出压缩包
binwalk -e test.bin
-D或者–dd 分解某种类型的文件
binwalk -D=jpeg test.bin
-M 递归分解扫描出来的文件(得跟-e或者-D配合使用)
binwalk -eM test.bin
exiftool
Ubuntu / Debian 系列
sudo apt update
sudo apt install libimage-exiftool-perl -y
安装完成后,可以通过以下命令验证:
exiftool -ver
输出版本号(如 12.76)即表示安装成功。